Phone cloning is quite popular in the entertainment industry. Movie producers make it seem like one of the easiest things you can do to spy on someone's activities. In reality, things are a bit different, in that phone cloning is not exactly easy to do.
But, that doesn't make phone cloning an impossibility, or even unlikely in some cases, especially since older phones are more susceptible to cloning than new ones. Here's what you need to know about how cloning works, what it can mean to you, and how to check if a device has been cloned.
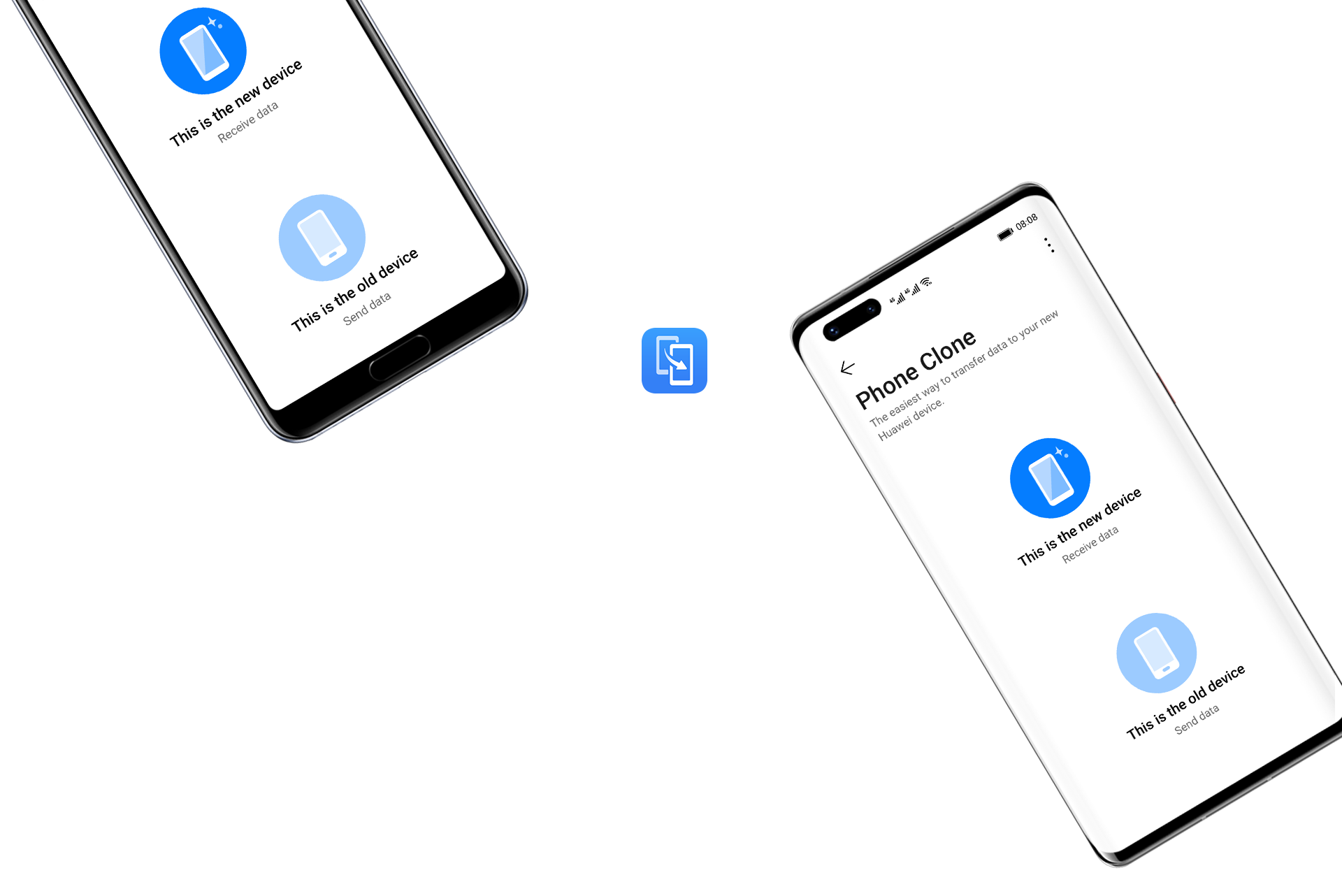
'Yasin used a software called Patagonia which can be used to clone only CDMA phones but there are software packages available in the market which can be used to clone even GSM phones. The first solution to how to clone a phone without touching it involves the use of a third-party tool that exploits a vulnerability on the target device. If the device that you wish to hack hasn't been updated in a while, then chances are it might be vulnerable to a Bluetooth security attack. Cell Phone Cloning software, free download - BlackBerry Desktop Software, Send To Phone, Macrium Reflect Free, and many more programs.
What Is Phone Cloning?
In the simplest of terms, phone cloning involves copying the identity of one mobile device in order to use it on another. Although there are three main methods of cloning, AMPS, CDMA, and GSM cloning, only the latter is more popular.
GSM cloning relies on identifying and copying the IMEI, or International Mobile Station Equipment Identity number. This is a unique identifier that can be obtained via hacking. Also in GSM cloning schemes you'll find hardware SIM card cloning. In most cases this would require physical access to the SIM card in order to extract its K code.
While phone cloning is illegal in most countries, phone cloning can still be a thriving industry. But, due to how complex some of the detection methods are, such as radio fingerprinting, very few users are in danger of having their phones cloned. Most modern smartphones are more susceptible to direct hacking than cloning.
How to Check if Your Phone Has Been Cloned
If your phone has been cloned through a very basic IMEI cloning method, you might be able to spot a duplicate using phone locating software like Find My iPhone (Apple) or Find My Phone (Android). Facebook auto liker for pc.
- Log into your account.
- Use the map to pinpoint your phone's location.
- Check for another or a duplicate marker.
If you see more than one device being pinged and you know you only have one phone, then it's possible that the secondary device is the cloned version of your phone.
Another method that might work involves going through all expenses on your bill. If you find discrepancies like calls to numbers you don't know, then your phone might have been cloned. You also don't have to wait until the end of the month to do this.
If you contact your carrier you could request a preliminary bill and start verifying the expenses. However, keep in mind that not all criminals clone phones in order to rake up bill charges. Some simply clone devices and wait for sensitive information to be sent or received via text, information that they can exploit for monetary gain.
How to Check If You're Using a Cloned Phone
It may be easier to tell if you're using a cloned phone than to tell if your phone has been cloned. Why would someone sell you a cloned phone? Well, there could be dozens of reasons, but the main one will always be profit.
To check if you're using a cloned phone you may want to start by paying extra attention to the incoming text messages and calls. Too many incoming calls and texts from unknown numbers and unknown senders, may indicate that you're not the sole owner of your phone and number.
You may also want to check the IMEI and serial numbers online, on the manufacturer's website. If they match then you should be the sole proprietor of that phone. If there are discrepancies, then chances are you're using a cloned, or at least a fake phone.
Another thing you could do is to check the build quality. Check it against an unboxed phone of the same model. Look for anything out of the ordinary regarding weight, accessories, existing software, OS version, and performance.

'Yasin used a software called Patagonia which can be used to clone only CDMA phones but there are software packages available in the market which can be used to clone even GSM phones. The first solution to how to clone a phone without touching it involves the use of a third-party tool that exploits a vulnerability on the target device. If the device that you wish to hack hasn't been updated in a while, then chances are it might be vulnerable to a Bluetooth security attack. Cell Phone Cloning software, free download - BlackBerry Desktop Software, Send To Phone, Macrium Reflect Free, and many more programs.
What Is Phone Cloning?
In the simplest of terms, phone cloning involves copying the identity of one mobile device in order to use it on another. Although there are three main methods of cloning, AMPS, CDMA, and GSM cloning, only the latter is more popular.
GSM cloning relies on identifying and copying the IMEI, or International Mobile Station Equipment Identity number. This is a unique identifier that can be obtained via hacking. Also in GSM cloning schemes you'll find hardware SIM card cloning. In most cases this would require physical access to the SIM card in order to extract its K code.
While phone cloning is illegal in most countries, phone cloning can still be a thriving industry. But, due to how complex some of the detection methods are, such as radio fingerprinting, very few users are in danger of having their phones cloned. Most modern smartphones are more susceptible to direct hacking than cloning.
How to Check if Your Phone Has Been Cloned
If your phone has been cloned through a very basic IMEI cloning method, you might be able to spot a duplicate using phone locating software like Find My iPhone (Apple) or Find My Phone (Android). Facebook auto liker for pc.
- Log into your account.
- Use the map to pinpoint your phone's location.
- Check for another or a duplicate marker.
If you see more than one device being pinged and you know you only have one phone, then it's possible that the secondary device is the cloned version of your phone.
Another method that might work involves going through all expenses on your bill. If you find discrepancies like calls to numbers you don't know, then your phone might have been cloned. You also don't have to wait until the end of the month to do this.
If you contact your carrier you could request a preliminary bill and start verifying the expenses. However, keep in mind that not all criminals clone phones in order to rake up bill charges. Some simply clone devices and wait for sensitive information to be sent or received via text, information that they can exploit for monetary gain.
How to Check If You're Using a Cloned Phone
It may be easier to tell if you're using a cloned phone than to tell if your phone has been cloned. Why would someone sell you a cloned phone? Well, there could be dozens of reasons, but the main one will always be profit.
To check if you're using a cloned phone you may want to start by paying extra attention to the incoming text messages and calls. Too many incoming calls and texts from unknown numbers and unknown senders, may indicate that you're not the sole owner of your phone and number.
You may also want to check the IMEI and serial numbers online, on the manufacturer's website. If they match then you should be the sole proprietor of that phone. If there are discrepancies, then chances are you're using a cloned, or at least a fake phone.
Another thing you could do is to check the build quality. Check it against an unboxed phone of the same model. Look for anything out of the ordinary regarding weight, accessories, existing software, OS version, and performance.
If your phone is not working as well as it should or if it's lighter than it should be, then you could be dealing with a cloned phone. Buying phones from unverified vendors or off Craigslist are just two of the ways in which you could end up with a cloned phone in your hands.
Cloning – Less of an Issue but Still a Troubling One
Patagonia Phone Cloning Software Online
There's not a lot of phone cloning going around these days since both carriers and hardware manufacturers have developed more advanced methods of combating this nefarious act. With that in mind, once your phone has been successfully cloned, you could be potentially subject to blackmail, identity theft, etc.
You might also have to face the fact that it could be impossible to determine whether or not your phone has been cloned. There are plenty of sophisticated cloning devices that may very well leave no traces behind. Let us know how you feel about phone cloning, how often do you think it happens, and what your thoughts are on prevention methods.
MOBILE PHONE CLONING
Faculty Mentor:
Dr. Deepshikha Aggarwal
Student Name:
Divya Farswan(MCA-II)
Sagar Gandhi(MCA-II)
Patagonia Phone Cloning Software For Android
1. INTRODUCTION
Mobile communication has been a readily available service from many years, and it is a major business today. It provides a valuable service to the users who are willing to pay a considerable amount over a fixed line phone, they are able walk and talk freely with the handset. Because of its usefulness to the masses and the money involved in the business, it is subject to risk which can result into fraud. Unfortunately, the advance of security standards has not kept pace with the dissemination of mobile communication.There is a chance you are the victim of mobile cloning. It is also known as cell phone piracy and has been taking place throughout the world for many years. Recently this crime has come to our country.Some of the features of mobile communication make it an alluring target for criminals. It is a relatively new invention, so not all people are quite familiar with its possibilities, in good or in bad.
1.1. CELL PHONE CLONING
Cell phone cloning is copying the identity of one mobile telephone to another mobile telephone. Usually this is done for the purpose of making fraudulent telephone calls. The bills for the calls go to the legitimate subscriber. The cloner is also able to make effectively anonymous calls, which attracts another group of interested users. Cloning is the process of taking the programmed information that is stored in a legitimate mobile phone and illegally programming the identical information into another mobile phone.The result is that the 'cloned' phone can make and receive calls and the charges for those calls are billed to the legitimate subscriber. The service provider network does not have a way to differentiate between the legitimate phone and the 'cloned' phone.
Fig 1: showing cellular cloning
2. THE CELL PHONE FRAUD
Cell phone fraud is defined as the unauthorised use of cellular phones. Customers have a new privacy threat to worry about and this is known as cell phone fraud. This can have a devastating effect on a person's personal life as well as on their finances. There are two major types of cellular frauds: subscriber fraud and cloning fraud.
2.1 Cell phone cloning fraud
You have to be aware of this cloning fraud in which when the crooks get a hold of your phone's unique serial number and 10-digit mobile number.Each cell phone should have a unique factory-set electronic serial number and telephone number. A cloned cell phone is one that has been reprogrammed to transmit the ESN and MIN belonging to another legitimate cell phone. Unauthorised people can obtain legitimate ESN/MIN combinations by illegally monitoring the radio wave transmissions from the cell phones of legitimate users.After cloning, both the legitimate and the fraudulent cell phones have the same ESN/MIN combination and become impossible to distinguish between fraudulent cell phone and authentic cell phone. The legitimate phone user then gets billed for the cloned phone's calls.
2.2 How big of a problem is cloning a phone?
It's safe to say that cell phones have become must-have gadgets for most of us these days. Because criminals know this, they're targeting cell phone users to acquire the maximum profit.It is about every year the mobile phone industry pays millions of dollars in revenue because of the criminals who reconfigure the cell phone so that their calls are billed and paid by the innocent users. But a cloned phone is also used for many kinds of illegal activities such as drug crimes. Since calls are not billed to their number, it becomes very difficult to trace them. Traffickers buy these cloned phones at cheap prices to make dozens of calls and throw it away after using them for a short period of time. In a similar way, terrorists have been using cloned phones to thwart law enforcements efforts aimed at tracking there where about.The Cellular Telecommunications Industry Association (CTIA) estimates that financial losses is due to cloning fraud are around 800 million dollar in USA. Some subscribers of Reliance had to suffer because their phone was cloned. Mobile Cloning is in its initial stages in our country so preventive steps should be taken by the Government as well as the network provider.
Fig 3: Selection of mobile phones that can be cloned
2.3 Cloning detection
Unfortunately, there is no other way for subscriber to detect cloning. Events like anomalies in monthly bills can act as tickers. There are some points mentioned below.
1) Continuous wrong number phone calls to your phone.
2) Difficulty in retrieving voice mail messages.
3) Difficulty in placing outgoing calls.
4) Incoming calls continuously receiving invalid numbers. Unusual calls appearing on your phone bills
3. TYPES OF CLONING
3.1 CDMA cloning
Code Division Multiple Access (CDMA) mobile telephone cloning involves gaining access to the device's embedded file system through a specialized software or placing a modified EEPROM into the target mobile, allowing the Electronic serial number(ESN) and/or Mobile Equipment Identifier (MEID) of the mobile phone to be changed. To obtain the Mobile Equipment Identifier of your phone, just open your phone's dialler pad and type *#06# to get the phone's MEID number.The ESN or MEID is transmitted to the company's Mobile Telephone Switching Office (MTSO) in order to check the authenticity of a handset onto the mobile network. Modifying the mobile phone's Preferred Roaming List (PRL) and the mobile identification number, or MIN, can pave the way for fraudulent calls, as the target telephone is now a clone of the telephone from which the original ESN and MIN data were obtained.
Fig 4: Basic CDMA cloning system
PATAGONIA- A cloning software
Patagonia is software available which is used only to clone CDMA phone. Using this software a cloner can take over the control of a CDMA phone and it is resulted into cloning of the phone. There are many more software available in the market to clone GSM phone. These software's are easily available in the market. A SIM can be cloned again and again and they can be used for different purposes. Messages and calls that are sent by cloned phones can be tracked.
3.2 GSM cloning
Cloning of a CDMA handset can be done easily, but it is quite challenging on GSM phones. However, cloning of a GSM phone is done by cloning the SIM card contained within, but it is not necessary to any of the phone's internal data. GSM phones doesn't have ESN or MIN, only an International Mobile Station Equipment Identity (IMEI) number. Since there are various methods by which we can obtain the IMEI number. The most common methods are to hack into the cellular company, or to eavesdrop on the cellular network.
Fig 5: GSM Authentication Protocol
4. REAL LIFE CASE
Few months ago Delhi police arrested a person with 20 laptops, a SIM card scanner, and multiple mobile phones. The criminal was taking care of an illegal exchange where he cloned CDMA based cell phones. He used a software named Patagonia which is specifically used to clone the CDMA cell phones and provided cheap international calls to Indian immigrants in South Asia. Later he was arrested and is serving himself in the prison for the cellular crime he committed.
5. Preventive measures and effectiveness
Authentication is the only industry standard way of avoiding cell phone cloning fraud. It is considered as one of the most robust and reliable method for eliminating phone cloning. Every cell phone contains a radio fingerprint in its transmission signal and the identity of the cell phone is checked by matching the fingerprint at service provider end while making a call. This fingerprint remains unique to the mobile phone despite of any change to the phone's ESN, IMEI, or MIN numbers. Therefore, when any discrepancies between the fingerprint and the ESN, IMEI, or MIN numbers are found, the cellular companies easily trace cloned phones.Service providers have adopted certain measures to prevent cellular fraud. This includes blacklisting, encryption, blocking, user verification and traffic analysis.Blacklisting of stolen mobiles is another way to prevent unauthorized use. An Equipment Identity Register enables network operators todeactivate stolen cellular phones on networks around the world.
User identification is done by using Personal Identification Number (PIN) code is one way for customer security against cellular phone fraud.
6. CONCLUSION
In today's world, India's mobile phone market has rapidly grown. It is one of the fastest growing market in the Indian economy. Mobile phones have become a major part of our day to day life and no one can survive without mobile phones. With the advancement of technology, better network availability, falling phone tariffs and handset prices making it one of the fastest growing market globally.
In our country mobile cloning is in initial stages so to prevent this condition strict steps should be taken by the network provider as well as the Government to prosecute crimes related to cellular phones, which currently is not viewed as a priority, In order to decrease this crime it is essential to incorporate cellular phone fraud, in particular 'CLONING FRAUD' as a serious crime.
7. REFRENECES
1. https://www.seminarsonly.com/Labels/Mobile-Phone-Cloning
2. https://en.wikipedia.org/wiki/Phone_cloning
3. https://fraud.laws.com/cellular-phone-fraud/cell-phone-cloning
4.ttps://www.phone.instantcheckmate.com/dialed-in/prevent-cell-phone-cloning/
5.https://www.chitkara.edu.in/wecon/newsletter/vol 2-issue6/
6. https://easytechnow.com/learn-technology/what-is-phone-cloning/

